Siemens USA, a manufacturer of industrial and health-care equipment, uses AIOps through its endpoint detection and response system that incorporates machine learning, the subset of AI that enables systems to learn and improve. The system gathers data from endpoints–hardware devices such as laptops and PCs–and then analyzes the data to reveal potential threats. The organization’s overall cybersecurity approach also uses data analytics, which allows it to quickly and efficiently parse through numerous log sources. The technology “provides our security analysts with actionable outputs and enables us to remain current with threats and indicators of compromise,” Mahmood says.
AIOps is a broad category of tools and components that uses AI and analytics to automate common IT operational processes, detect and resolve problems, and prevent costly outages. Machine-learning algorithms monitor across systems, learning as they go how systems perform, and detect problems and anomalies. Now, as adoption of AIOps platforms gains momentum, industry observers say IT decision-makers will increasingly use the technology to bolster cybersecurity–like Siemens, in integration with other security tools–and guard against a multitude of threats. This is happening against a backdrop of mounting complexity in organizations’ application environments, spanning public and private cloud deployments, and their perennial need to scale up or down in response to business demand. Further, the massive migration of employees to their home offices in an effort to curb the deadly pandemic amounts to an exponential increase in the number of edge-computing devices, all which require protection.
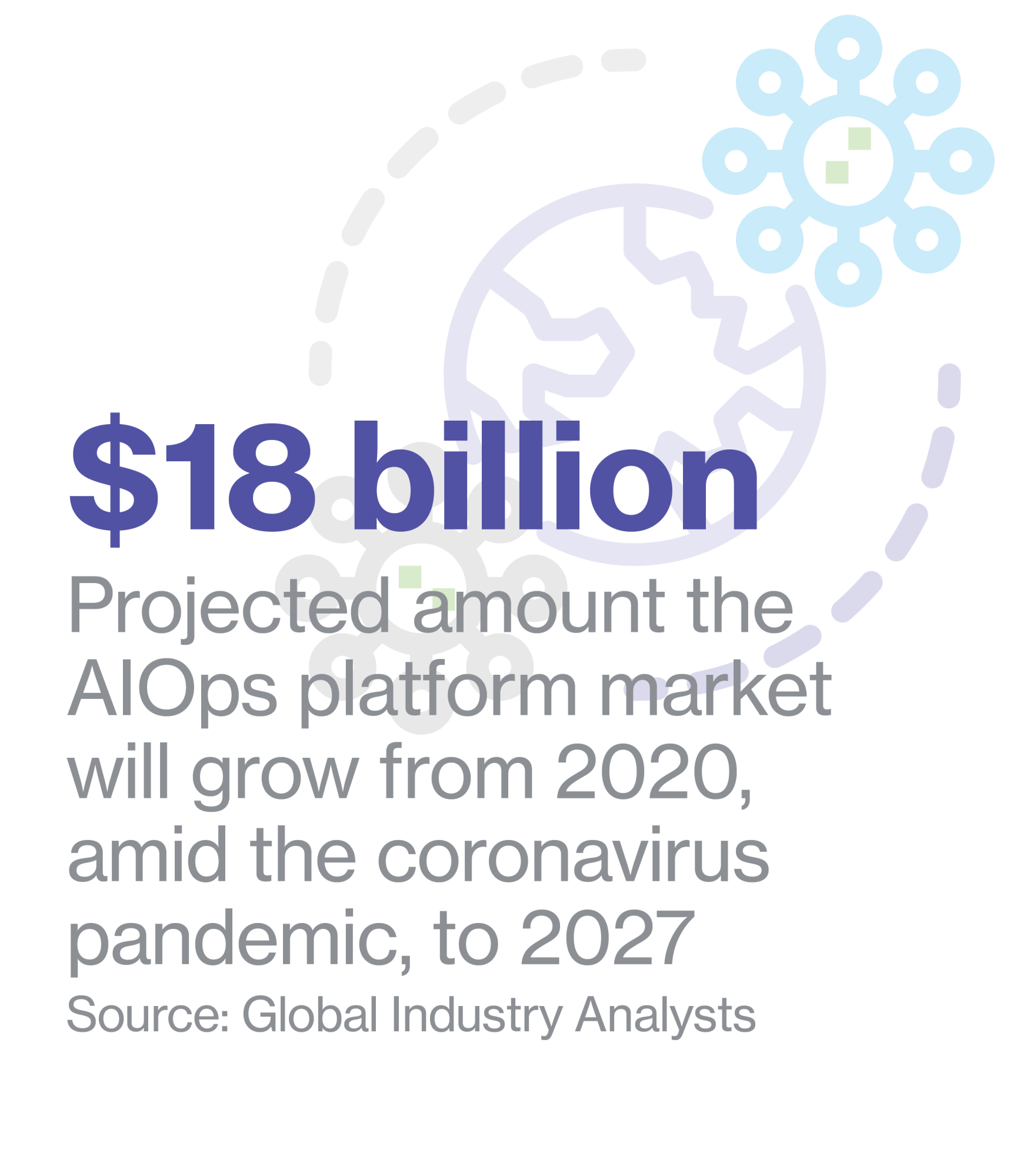
A May report from Global Industry Analysts predicts the AIOps platform market worldwide will grow by an estimated $18 billion this year, driven by a compounded growth rate of 37%.1 It also projects that AIOps initiatives–particularly among big corporations–will span the entire corporate ecosystem, from on-premises to public, private, and hybrid clouds to the network edge, where resources and IT staff are scarce. Most recently, a well-documented rise in data breaches, particularly during the pandemic, has underscored the need to deliver strong, embedded security with AIOps platforms.
Faster than a speeding human
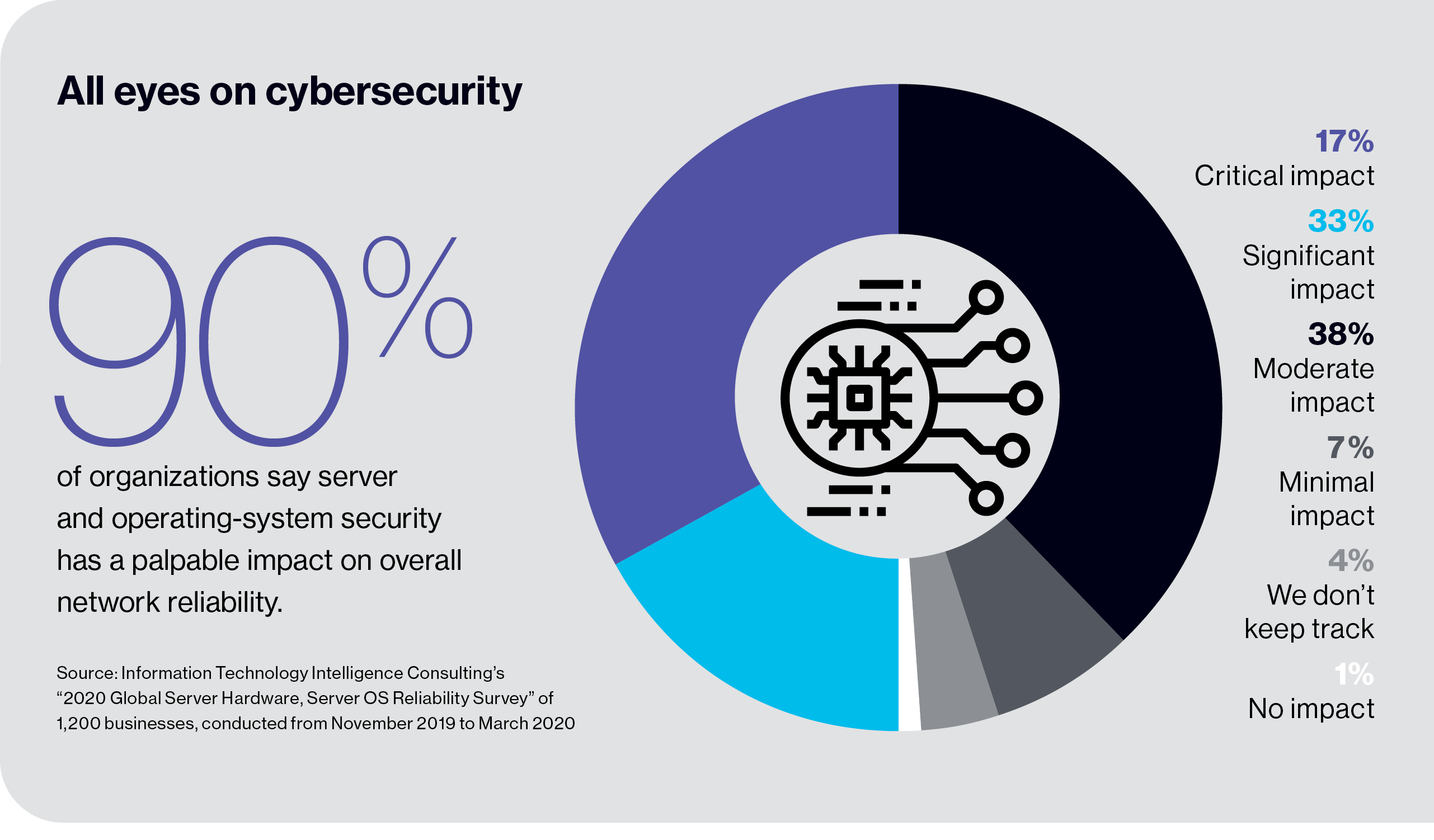
Cybersecurity affects every aspect of business and IT operations. The sheer number of near-daily breaches makes it difficult–if not impossible–for organizations, IT departments, and security professionals to cope. In the last year, 43% of companies worldwide reported multiple successful or attempted data breaches, according to an October 2019 survey conducted by KnowBe4, a security awareness training company.2 Nearly two-thirds of respondents worry their organizations may fall victim to a targeted attack in the next 12 months, and today concern is further fueled by the growing number of cybercrimes amid disarray caused by the pandemic. Organizations need to use every technological means at their disposal to thwart hackers.
The strongest AIOps platforms can help organizations proactively identify, isolate, and respond to security issues, helping teams assess the relative impact on the business. They can determine, for example, whether a potential problem is ransomware, which infiltrates computer systems and shuts down access to critical data. Or they can ferret out threats with longer-term effects, such as leaking customer data and in turn causing massive reputational damage. That’s because AIOps platforms have full visibility into an organization’s data, spanning traditional departmental silos. They apply analytics and AI to the data to determine the typical behavior of an organization’s systems. Once they have that “baseline state,” the platforms do continual reassessments of the network–and all wired and wireless devices communicating on it–and zero in on outlier signals. If they’re suspicious–exceeding a threshold defined by AI–an alert is sent to IT security staffers detailing the threat, the degree to which it could disrupt the business, and the steps they need to take to eliminate it.
Download the full report.


